Hi! Here’s Something about Maze Ransomware!
This is to tell you with respect to an ongoing Ransomware Attack ( Maze – Ransomware ) which influences one of the main IT organizations. In light of a portion of your solicitations, IARM Cyberattack Recovery services made a Detail about the assault and Prevention. Expectation this may assist you with avoiding digital dangers and potential dangers which is probably going to make a disturbance in business.
Mercifully read the underneath focuses which gives an elevated level outline of the cybersecurity best practice and suggestions as nitty-gritty.
In the event that you might want to find out about this Alert and fixes, kindly connect with us at IARM Information Security | info@iarminfo.com | https://www.iarminfo.com/
Abstract
Like all ransomware, the principle objective of the Maze is to encode all documents that it can in a contaminated framework and afterwards request a payoff to recuperate the records. In any case, there are things that are not all that basic to Maze Ransomware that we have to think about
1. Found on May the 29th 2019 by Jerome Segura. [Malware Wiki]
2. The aggressor compromises the casualties that; in the event that they don’t pay, they will discharge the data on the Internet. Labyrinth’s administrators have made a devoted website page, which records the characters of their non-agreeable casualties and routinely distributes tests of the taken information. The labyrinth has since distributed the subtleties of many organizations.
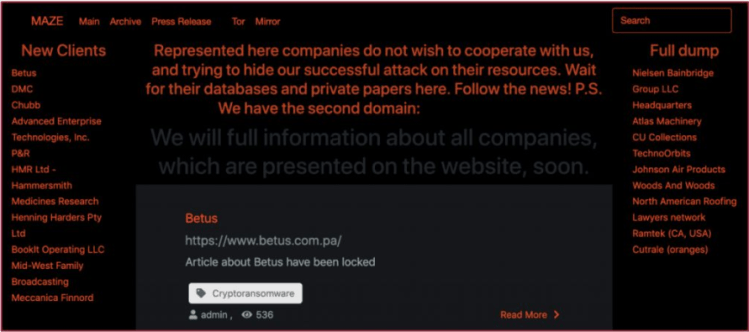
3. Pointer Of Compromise (IOCs) that one of the ongoing casualties has given incorporated the IP locations of servers related with the kepstl32.dll, memes.tmp and maze.dll records, which are known to be utilized beforehand in Maze ransomware assaults. Henceforth it is suspected that they could do focused on assaults, dissimilar to wanacry which was intended to spread by abusing Eternal Blue weakness.
4. Similarly, as with numerous kinds of ransomware, there is an idea to unscramble three pictures for nothing and that administration has been confirmed as working, which shows the verification of decoding to bait the person in question.
A Brief Technical Details in 6 stages
1. The PEB field “IsDebuggerPresent”. This field is a Boolean field that is filled from Windows with 1 (True) if the application is running within a debugger or 0 (False) on the off chance that it isn’t. In the event that the malware distinguishes a debugger, it will stay in a boundless circle without making anything while at the same time squandering framework assets.
2. It can end IDA debugger, x32dbg, OllyDbg and more procedures to evade dynamic examination, close databases, office projects and security apparatuses
3. The malware attempts to erase the shadow volumes in the framework utilizing the “wmic.exe” program with the switches “shadow duplicate” and “erase”. Preceding this, the malware gets the capacity of “WoW64DisableWow64FsRedirection” with “GetProcAddress” and utilizations it to stay away from redirection as a matter of course in 64-piece working frameworks and calls it in a unique manner.
4. The malware attempts to erase the shadow duplicates multiple times, once before encoding the records in the contaminated framework and besides in the wake of scrambling them.
5. The malware utilizes two calculations to encode the documents, ChaCha which depends on the Salsa20 calculation that is symmetric and, for insurance, an RSA calculation that is unbalanced.
6. In every execution, the malware makes a Public BLOB of one RSA key that will be utilized to sepulchre the part that holds the data to unscramble the documents and one Private BLOB with an RSA key that permits decoding of the data encoded with the open RSA mass made already.
Is it accurate to say that you are wanting to diminish your current cost in the Information/Cybersecurity domain? We can guarantee you that you will get quality help at less cost. IARM Information Security, one of only a handful scarcely any organizations in India to concentrate only on End-End Information Security arrangements and administrations.
Purpose of interruption
This Ransomware is known to spread by means of email connections by utilizing (satirizing) notable and believed area names
Suggestion
1. Inform end clients to abstain from opening any suspicious messages and open connections from obscure sender/source. The equivalent goes for joins in messages
2. Update most recent security Patch for all gadgets and OS
3. Strongly prescribe to Implement SIEM apparatus and track security occasions
4. Update most recent Anti-Virus signature
5. Incapacitate macros in Office programs and never empower them except if it is fundamental to do
6. Reinforcement every basic document utilizing 3-2-1 principle. 3 reinforcement duplicates on 2 distinct media with 1 reinforcement in a different area
7. Handicap RDP. In the event that your association must utilize RDP, abstain from presenting it to the open web. As it were gadgets on the LAN or getting to by means of VPN, ought to have the option to build up a remote meeting
If you have any queries, feel free to contact us IARM Information Security | info@iarminfo.com | https://www.iarminfo.com/
Thanks and Regards
Priya Dharshini
IARM Information Security – Penetration Testing Services | VAPT Services | Cyber Attack Recovery Services | Business Continuity Management services